Have you ever been hit by Ransomware? Do you even know what Ransomware is? Regardless if you answered yes or no...this is good info to have.
First, lets start off with what Ransomware is. Regardless of how it happens, the methodology is the same in that your data (regardless of what it is) is encrypted and then held for ransom. You are told to pay the ransom, normally via bitcoin, in order to get the decryption key. Quite often the ransomer has no idea how much was encrypted so wouldn't know if it was one machine or an entire network. Although ransom technology is changing so more of that may come to light. Once ransom is paid, a smart ransomer will hold of before accessing bitcoin.
Unfortunately it's not that easy though. In the criminal underworld, there is a slight bit of honor among thieves. In other words, if someone is going to hold your data ransom and then never give you your decryption keys then there is no real reason to pay the ransom right? As it is, there is about a 70% rate of receiving decryption keys meaning that 30% of the time the criminals either don't give you the keys or give you the wrong keys. Thus, there is a bit of a gamble if you choose to pay.
Currently, what the FBI is recommending, is that you contact the FBI to determine a few things. First, you need to let them know what is going on. Second, the FBI may already have decryption codes from a prior case. Lastly, The FBI tracks these things so they are likely to let you know if you pay a ransom if you will get good results.
So what some companies are doing is, as a part of an incident response (IR) plan, is have $5K bitcoin ready to go and authorization to use it by the IR manager. The reasoning is that if a ransom of $300 is going to release quite a bit more of valuable data then to go ahead and pay the ransom as the cost of investigating and everything else with manually recovering the ransomed data. To us, this seems like a good idea as well as reducing the amount of red tape to go through at the last minute. Of course, we aren't condoning paying a ransom, but if $300 is all it takes to make a $100K problem go away...seems like good business sense.
However, one thing you absolutely must consider before paying a ransom...and that is who you are exactly paying. Should the ransomer be associated with a terrorist organization then "technically" you would be supporting a terrorist organization which can result in serious company and individual issues including incarceration.
So, who makes a good target? Well, those that are forced to remain on legacy operating systems for one. Or those that have slow update cycles due to some sort of mission critical dependencies where updating or patching could create risk. Hospitals make a prime target due to the fact that if they update too quickly then they may cause an issue that would put a life in danger. So the hospital has an aversion to staying on the cutting edge of updates. On the flip side if the hospital updates too slow then they become more of a target and, maybe, some complacency starts to naturally develope with the IT staff.
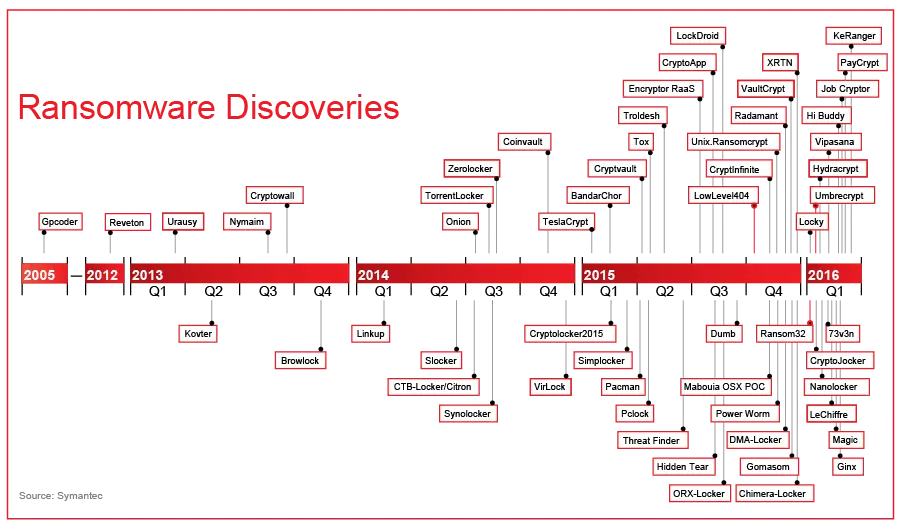
RansomWare will certainly evolve over time as defenses and user education increases. Having said that, the evolution is fast. See below with a sample evolution chart of ransomware.

The above graphic clearly shows a rapid increase of RansomWare as well as an evolution of RansomWare, per year, to increase the effectiveness of the RansomWare. Even though this graphic only shows 2005-2016, RansomWare has been around since 1989, it just wasn't popular or newsworthy then. RansomWare is even offered "as a service" by some of the more advanced cybercriminal organizations as well as easier to deploy RansomWare agents.
As time moves on, you will see more of an advanced evolution of RansomWare. Possibly RansomWare that is transmitted via Bluetooth and ransoming a phone, iDevice, or some other IoT type device such as a TV or refrigerator. Imagine a BT capable RansomWare that can interface with your car and disables your ability to drive your $50K car. Don't rule out WiFi and everything transmitting through that as well; WiFi makes a natural conduit for connectivity and dangerous malware transmissions.
What you can do to help yourself, assuming within budget, is versioning, read only snapshots of critical servers, and secure backups. The more money you spend up front to prevent the problem will only save money on the backend. This, primarily, is because the estimated cost for company wide downtime is $8,600 per hour for a $0-50MM sized company and $700K per hour for a company over $1BB per year.
Arrakis can help you avoid RansomWare and also act as a trusted agent or advisory during your difficult time of dealing with RansomWare. If you are in trouble, give us a call.